
Following my post last week, I decided to create a batch script that would let you see if your anti-virus product is also vulnerable to the “Vista Rootkit.”
You can download the script from here (Right-click, Choose “Save As.”)
Essentially, the script creates two identical files on your C:\ drive, in the C:\vistarootkit_test\ folder. These files contain contain a benign (read: non-viral) string of text that’s picked up by anti-virus products from all the leading companies. You can obtain more information on the test files here.
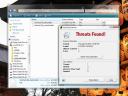
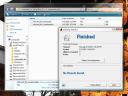
If the script works right, and your anti-virus product akin to mine, then it will pick up the “infected_file_detectable” (left image), but not the “infected_file_undetectable” (right image.)
What’s happening: Windows has a funky way of handling administrator accounts. Users, for instance, can chmod files to deny any other user read/write access to a set of files. What sets Windows apart from other operating systems in this regard is it’s adherence to these permissions for it’s root account equivalents – the Administrator/SYSTEM/etc. It is this fact which is being taken advantage of here.
By creating a dummy account, malware is able to run an instance of itself under that account, and deny read/write permissions to its files to all other accounts. This means that when home users run their anti-virus products, their AV will be denied read access to the malicious files. Meanwhile, the malware is able to continue to operate freely.
This demo script creates 2 identical files that should be picked up by any popular anti-virus product, and creates a new user account “viral_account.” It then sets the permissions for one of these files such that the viral_account has full access to it, but all other system accounts are denied access. When the anti-virus program is run, it should skip over the file whose permissions were edited, as it will be denied read access to the said file.
A simple way to rectify the issue would be for anti-virus products to modify the permissions of the files to grant itself access (Administrator accounts can do this – though they can’t read the file itself), screen it for known viral signatures, and then restore the file to the original permissions.
Comments
2 responses to “Is your anti-virus product deceived by the “Vista Rootkit”?”
By creating a dummy account, malware is able to run an instance of itself under that account…
Malware can’t create a dummy account.
The command in the batch file:
net user viral_account /ADD
fails when run from a standard user account.
True, except that 99% of home Vista users aren’t on standard user accounts… they’re running admin accounts. Typically you’ll only see user accounts in work environments, where the computers are the responsibility of a third party.
As an inadvertent case example – Cygwin created one such dummy account for it’s SSH server daemon, and the files it created assigned with sole permissions to that account were undeletable with my admin account. I had to reassign the files permissions in order to do anything with the said files.